Phishing happens!
Disclaimer: This is not particularlized, foolproof IT advice. We do NOT recommend that you “DIY” your company’s information security systems. Things change too quickly.
Nevertheless, I know that many of you will not heed that advice and instead will take a calculated risk and DIY-it anyway. So this is just my two cents. Maybe it will be useful – maybe not.
Was catching up on some admin today and as I clicked “send” on some of my client invoices, I realized that for all of the work that I do advising clients who have experienced phishing-related cyber incidents, I sure do send them a lot of things that say, implicitly or explicitly, “click here.”
Warning: It’s a bad idea.
Some of the most robust endpoint screening technologies remove links altogether, block non-whitelisted URLs, and pull together a barrage of technologies.
So while there are many excellent and affordable automated systems, there is always the core human element that is the weakest link in a security system.
Step 1: Check the headers.
Hover over or toggle down the little gray “v” at the email sender and confirm the address is an exact match. Yes, the Internet is full of weird things but the email address is a real thing.
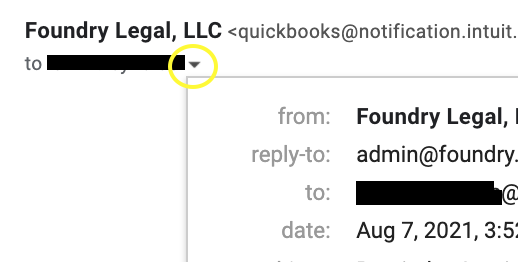
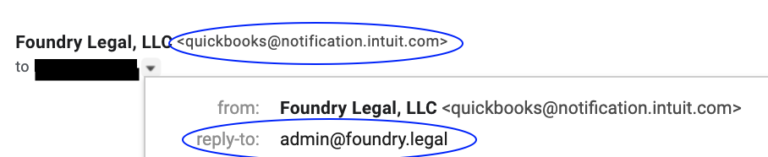
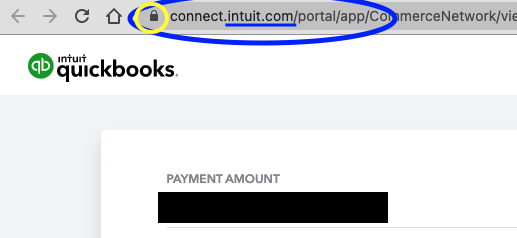
Step 2: Watch the URL.
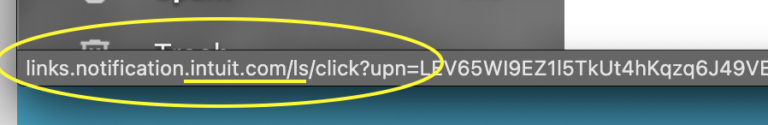
There’s like a button in your email that is hyperlinked. It will be shiny and hypnotic and will entice the user to click here. Seriously, there’s all sorts of science around these “call to action” buttons because they want the viewer to be hypnotized into doing exactly what the email sender/drafter requests: comply. Anyway, you can be cooler than James Gordon, and break the spell simply by pausing and checking the URL:
Is the domain what it should be ?
Often hackers will buy a domain with similar-looking spelling to a legitimate payment landing page. Just swap out an “i” for an “L”, or make the page “inntuit” in lieu of “intuit,” and most people never think twice. It’s also hard to catch if you never *look* at the site.
Too many Gotham references? Ah well.
Step 3: Really watch the money.
OK, so you’re ready to hit send. BUT BEFORE YOU DO: Do you *Really* know this vendor? Have you sent payments to them before via this method? Have you spoken to them by phone and know that this online request would be coming your way?
Many times I’ve gotten a phone call 48 hours a well-suspecting employee authroized a wire transfer to a new vendor, without having ever (1) spoken directly to the vendor, or (2) spoken — and I do mean speak, as in real time, voice / video conversation, not an email — to their *boss* about the payment that they later initiated to Mr. Bad Guy with an overseas account.
So what I’m saying is that if you ever get an email from “HeadHoncho@yourcompany.com” saying to “Please immediately wire $765,000 to a brand new vendor in Singapore, to help close an exciting new deal for the company!” consider the possible alternatives.
Wire transfers are nearly impossible to reverse. International wires, REALLY nearly impossible. Otherwise you might end up a very sad panda. 🙁




